Restaurant management made easy
We’ve Found the Elixir.
Market-Leading Tech. Local Support.
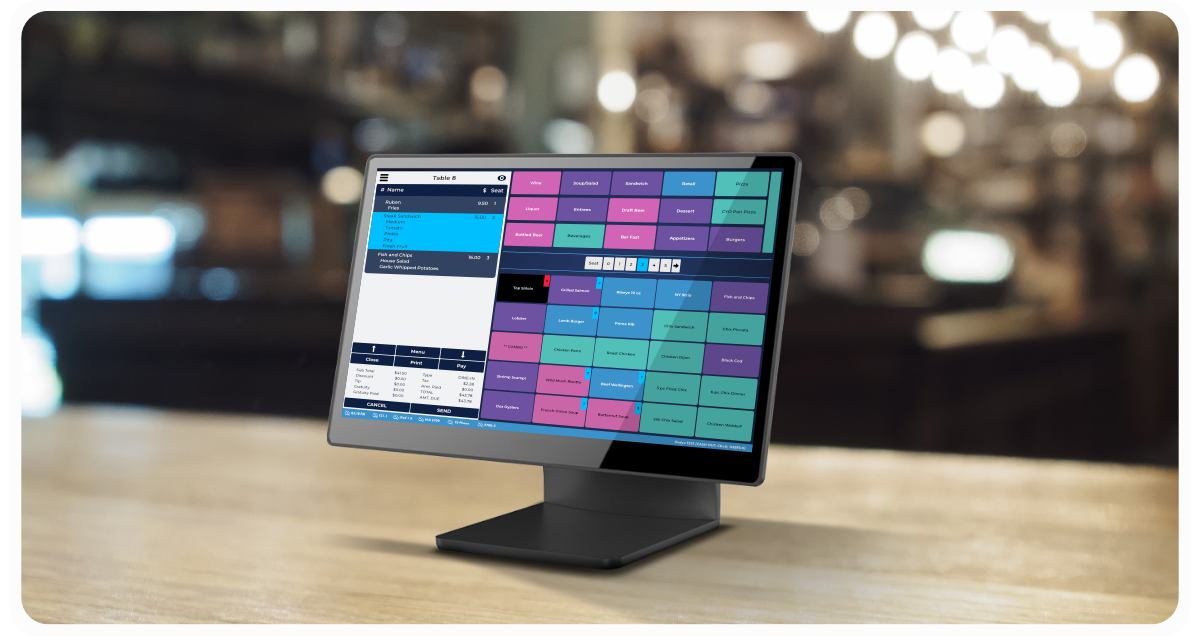







Add Tonic to Your Restaurant Systems

Cloud Connectivity
From the first minute your tonic system is installed, your receipts, guest checks, menus, timesheets and everything else that makes your business run will be secure and accessible on the cloud from all your devices.

Advanced Integrations
Tonic is built to pair seamlessly with your favorite software like Quickbooks, HotSchedules, Restaurant365, and many others ensuring maximum efficiency, improved accuracy and enhanced analytics, keeping your front office, back of house and floor on the same page.

Security & Compliance
Tonic’s security exceeds industry standards across the board. Your customers’ data and payment methods will be safeguarded throughout the payment capture process, ensuring you stay PCI compliant at every step.
For Your Guests
For Your Team
For Yourself
Tableside Service
Secure Transactions
Simplified Ordering
Integrated Reservations
Rewarding Loyalty Schemes

Tableside Service
Whether you’re taking a payment tableside or at the register, you’ll get the same speedy service throughout your establishment. Even tableside transactions won’t have to sacrifice options like eco-friendly digital receipts or customizable tipping.

Secure Transactions
Tonic’s security exceeds industry standards across the board. Your customers’ data and payment methods will be safeguarded throughout the payment capture process, ensuring you stay PCI compliant at every step.

Simplified Ordering
This is a fully modern point of sale system that allows your customers to place orders with your waitstaff or online via their own smartphone.

Integrated Reservations
Now the system that serves your tables is the same system that reserves your tables. Everything you need to seat and help your guests is in the same place.

Rewarding Loyalty Schemes
The best place to reward your regulars is within your Tonic POS. Keep track of all your points, offers and freebies in one, integrated place.
Customizable for Unique Needs
Streamlined Order Management
Simplified Scheduling
Training and Support
Intuitive and Reliable

Customizable for Unique Needs
You and your local partner can customize Tonic in infinite ways to make it work for the realities of your business and the market you reside in.

Streamlined Order Management
Not only do you get real-time inventory numbers, you’ll be able to control ordering, usage and more all from your smartphone. Plus, as a part of our comprehensive reporting system you’ll have all the data you need to track and adjust.

Simplified Scheduling
Keep your team on the same page in the same playbook with scheduling from Tonic. With historic and real time data at your fingertips, you’ll be able to ensure you have the right staff in place for every shift.

Training and Support
Unlike some POS systems, Tonic would never leave you to figure everything out yourself. With the help of our corporate team and local partners we’ll ensure your staff understands how to succeed with our system and what to do if they encounter hiccups.

Intuitive and Reliable
Our user experience is designed with your busy staff in mind. It’s easy to use and backed up by reliable, tested-and-true hardware to keep your team working.
Real-Time Remote Access
Multi-Location Management
Local Partners
Fully Serviced Installation and Maintenance
Third Party Integration

Real-Time Remote Access
Whether you want to be able to work from home or just the ability to check the bottom line from a coffee shop around the corner, with Tonic’s remote access you’ll have the ability to see what’s important when it’s important. You’ll be able to see the big picture of your data and get real time updates on the details of the dinner rush in the same place.

Multi-Location Management
Our scalable, multi-location solution makes sure every outlet in your organization is running in sync. You’ll be able to manage staffing, inventory, ordering, scheduling and accounting from one central hub.

Local Partners
The only way to get localized troubleshooting is to have the support of a truly local team. Our local partners have the technical expertise to service your network and machines with the regional savvy to make sure it will work for you.

Fully Serviced Installation and Maintenance
Ensure security, compliance and ease of use with our fully serviced installation and maintenance of your network and system. Whereas other system’s tech support stops at the plug, Tonic is a holistic solution to keep your system up and running.

Third Party Integration
Tonic blends well with the technical solutions you already love. Our software seamlessly pairs with apps like Chowly, Restaurant 365, QuickBooks and more.
What Makes Us Different
Restaurants and bars no longer have to choose between impersonal, multi-national POS systems or substandard local tech. With Tonic, you get industry-leading POS software and the experience, wisdom and support of certified, local partners who will be there with you from installation, through troubleshooting and every day thereafter.

We Love Our Customers
And They Love Us Too.

We like supporting the locals. Tonic are always right there if we ever have any questions.

Caitlin Pruitt
Calapooia Brewing Co.

They’ve made it very easy, as a first time restaurateur, to move through the system, learn it, work with it and train others. I would highly recommend this system to any other company.

Hector Chavez and Nena Chavez
Orenco Station Grill

Some of the pandemic stuff they did for us got us through. We didn’t do online ordering at all until Tonic saved us.

Morgan
The Brass Monkey

